Scareware
Problems
Scareware is a branch of the scam family, and has been around now for many years. For the most part, scareware is not automated and requires some action on your part to become active. Therein might lie the source of the problem.
In its simplest form, scareware either alarms you or pretends to do something that requires your attention, usually by clicking through something or other, known as 'clickjacking'. At that point, you have handed control of your computer or device to someone who may do something harmful to it. Or worse, you provide something you really should keep private, like credit card details to 'buy' a cure. The fix is easy - don't click anything, even a 'Close' button, in the body of the web page or e-mail.
Registry checkers and cleaners are a popular scare. Very few people know much about the registry, fret about having a backup, and have read enough scary articles about the end of the world being nigh to abandon common sense. Left alone (as in untouched by human hand) registry entries are very sturdy and can be left to do their own thing.
The other main theme at present is driver updates. At first blush, these seem reasonable offerings. But screen designs are deliberately confusing (which button do I click?) and, again, you hand over a degree of control to someone you've never met. If you have a driver problem, go to the hardware manufacturer's website and start from there. Remember that very few devices get driver updates in their lifetime, so the odds are in your favour.
The final and most dreadful variation on this them is ransomware. "We have locked your computer and will unlock it for $xxx" There have been reports of this in Australia. It is usually not a total lockout, but it can purport to affect certain key files and throw up a warning message. Experiences of this suggest that very few files get affected and the warning messages are not real. But this is not a happy situation.
Solutions
The difficulty is how to deal with problems. Most attacks are mounted on the administrative account, which usually belongs to the owner of the computer. Some users create a second admin account to give them a way in to their computer that isn't tainted, but that's not common.
To get around the brick wall of the admin account, go into Safe Mode (F8 during startup for XP, Vista, Win 7 - Shift plus F8 then 'See advanced...', 'Troubleshoot' and 'Advanced Options' in F8). Now you can use something like Windows Security Essentials/Defender to go looking and, hopefully, cleaning. There is an offline version of this if you need it.
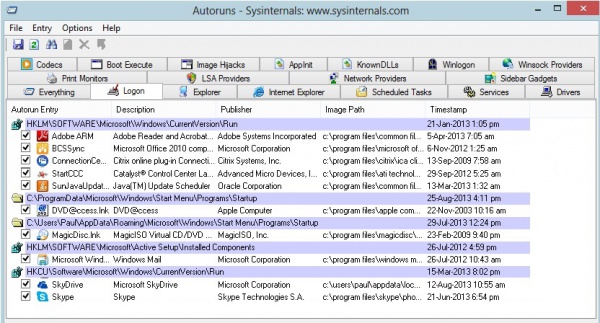
If all that fails, try Sysinternals Autoruns ([1]). To quote the blurb:
"This utility, which has the most comprehensive knowledge of auto-starting locations of any startup monitor, shows you what programs are configured to run during system bootup or login, and shows you the entries in the order Windows processes them. These programs include ones in your startup folder, Run, RunOnce, and other Registry keys. You can configure Autoruns to show other locations, including Explorer shell extensions, toolbars, browser helper objects, Winlogon notifications, auto-start services, and much more. Autoruns goes way beyond the MSConfig utility bundled with Windows Me and XP.
Autoruns' Hide Signed Microsoft Entries option helps you to zoom in on third-party auto-starting images that have been added to your system and it has support for looking at the auto-starting images configured for other accounts configured on a system. Also included in the download package is a command-line equivalent that can output in CSV format, Autorunsc."
Choose the Logon tab and see what is loading when the system boots. You can adjust things that you might not want...but, as ever, be careful.
You don't even need to download it, you can run it (safely) from the website. But it would be a good idea to put a copy on your hard drive so you can reach it when in difficulty. I'd run it weekly so nothing sneaks under your guard.
The reference to Windows Me is startling! But the utility has had regular updates since then.